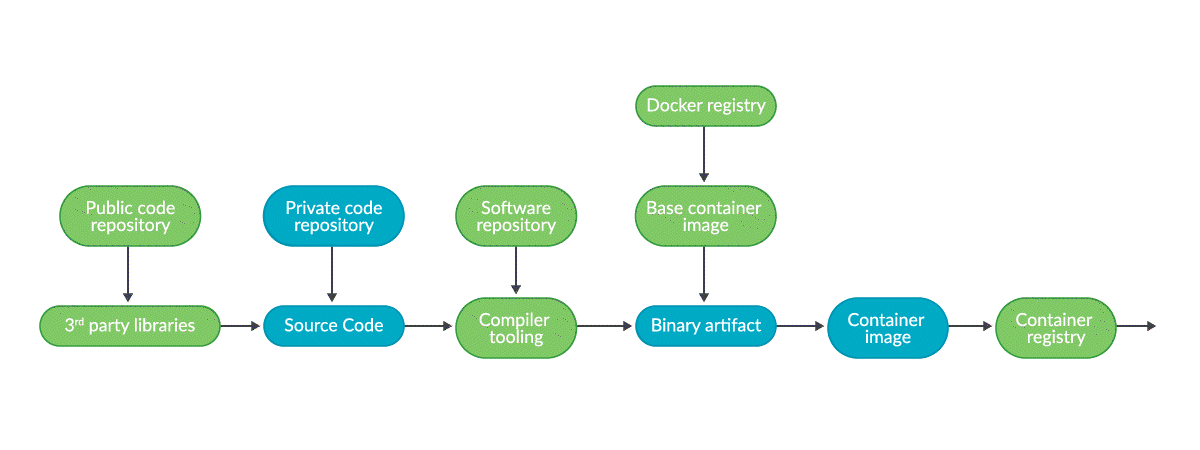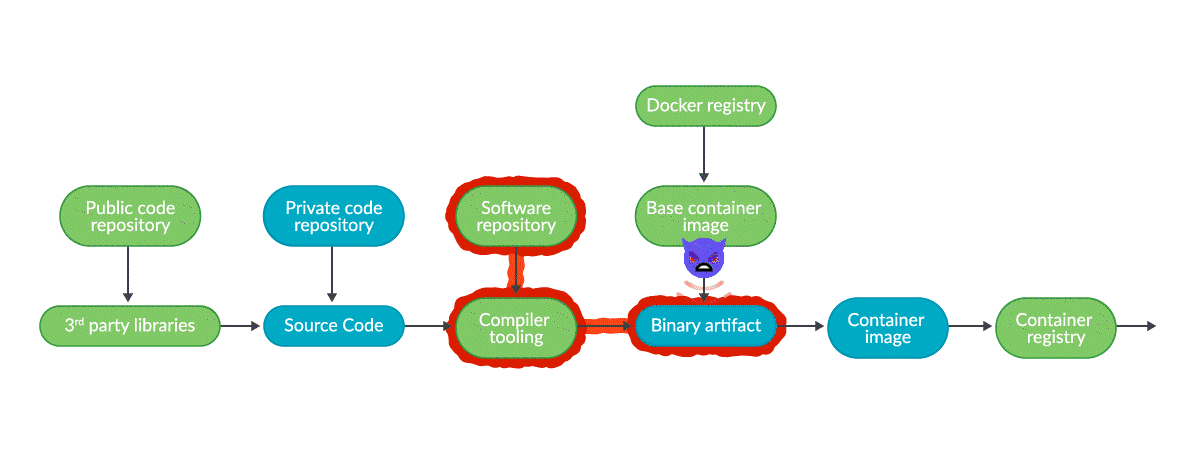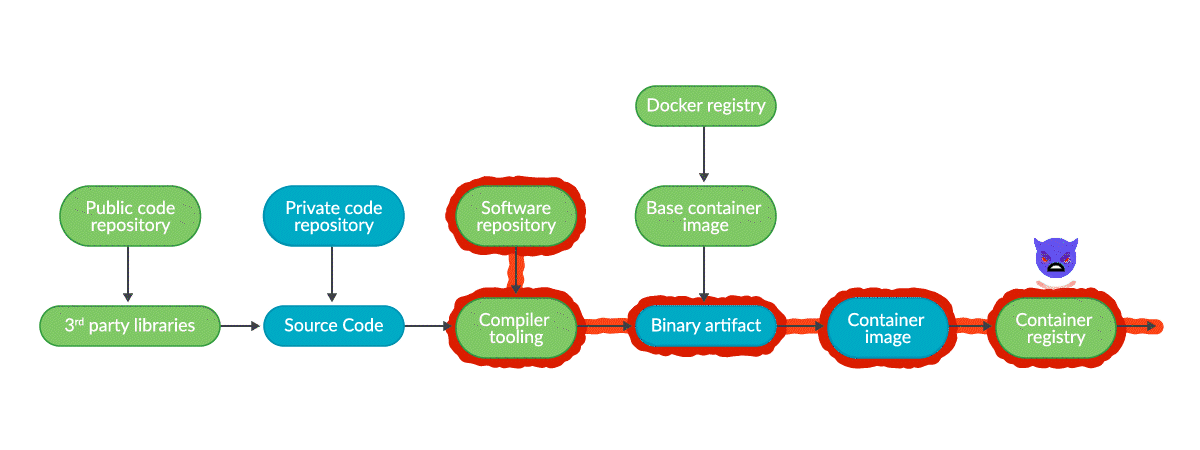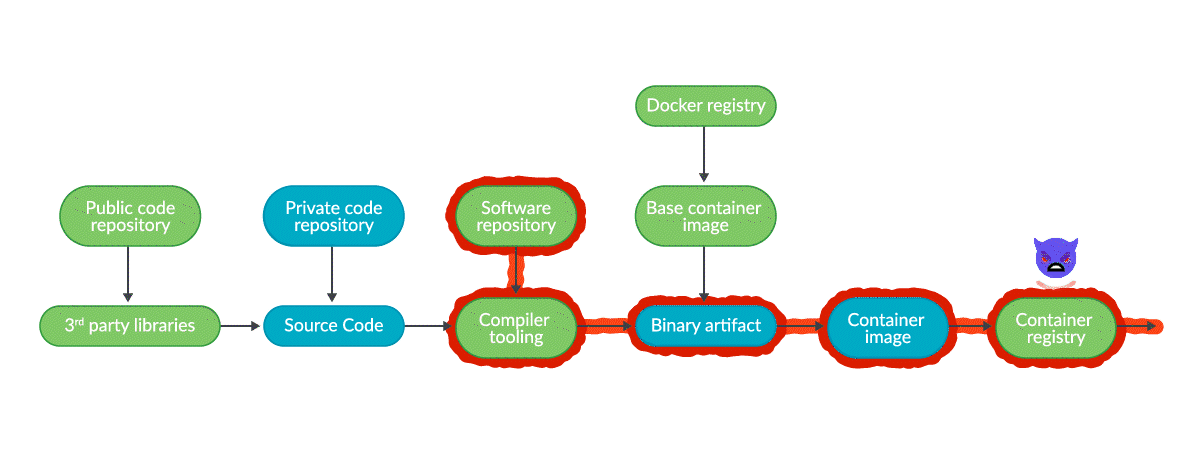
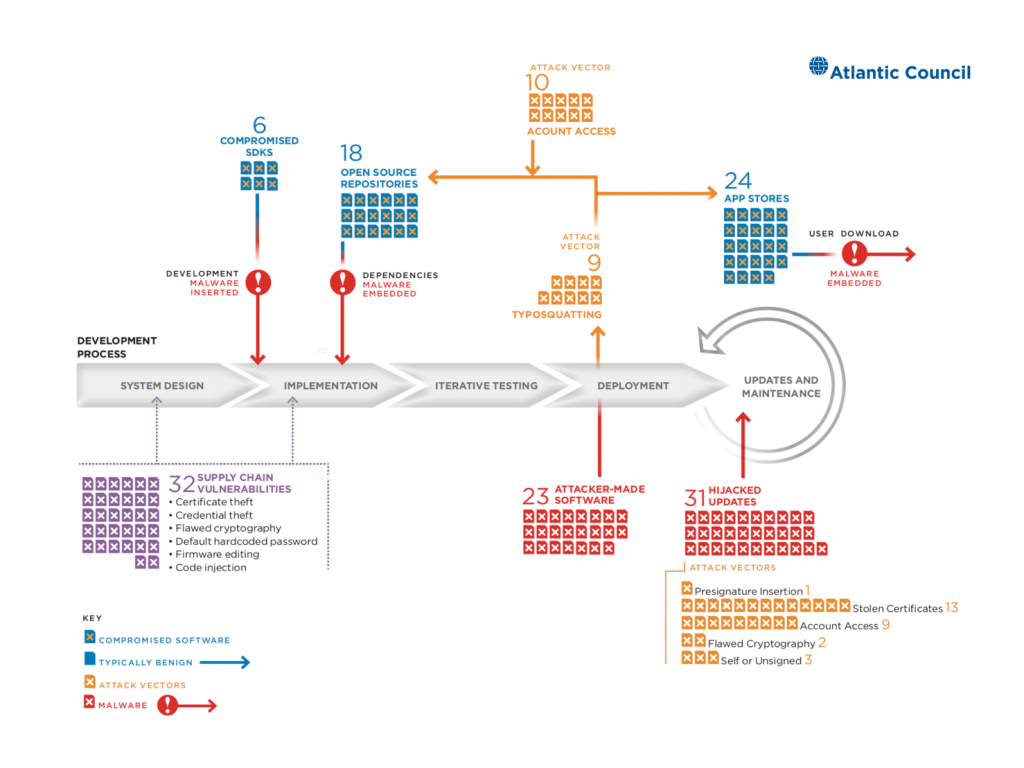
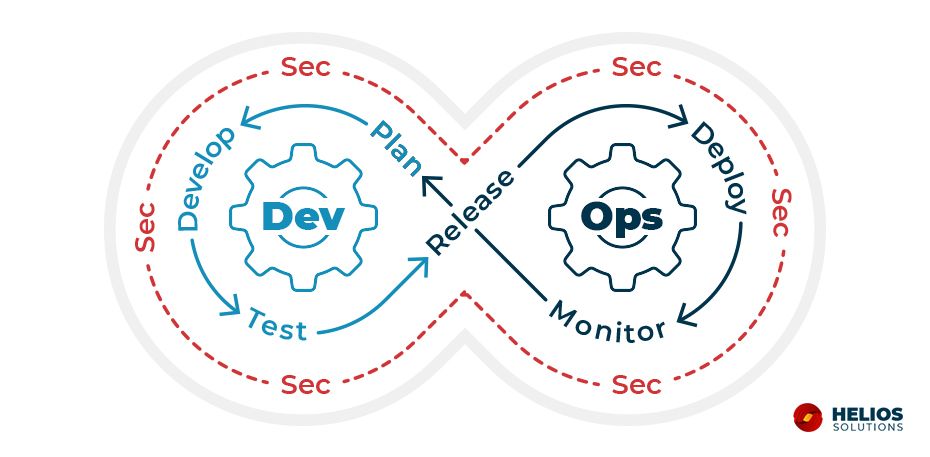
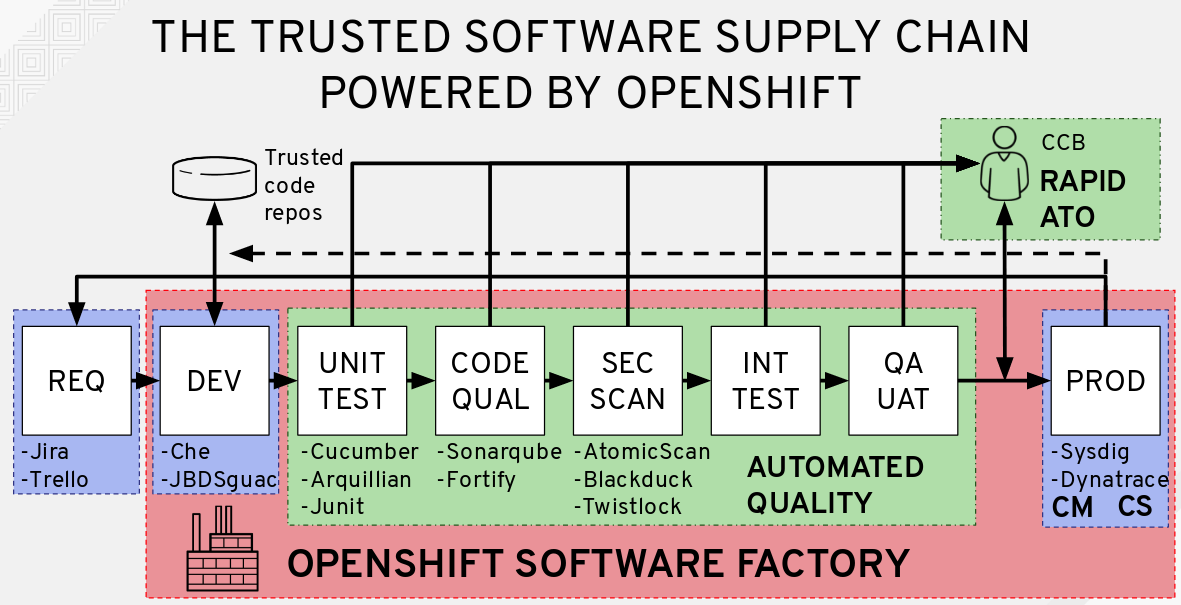
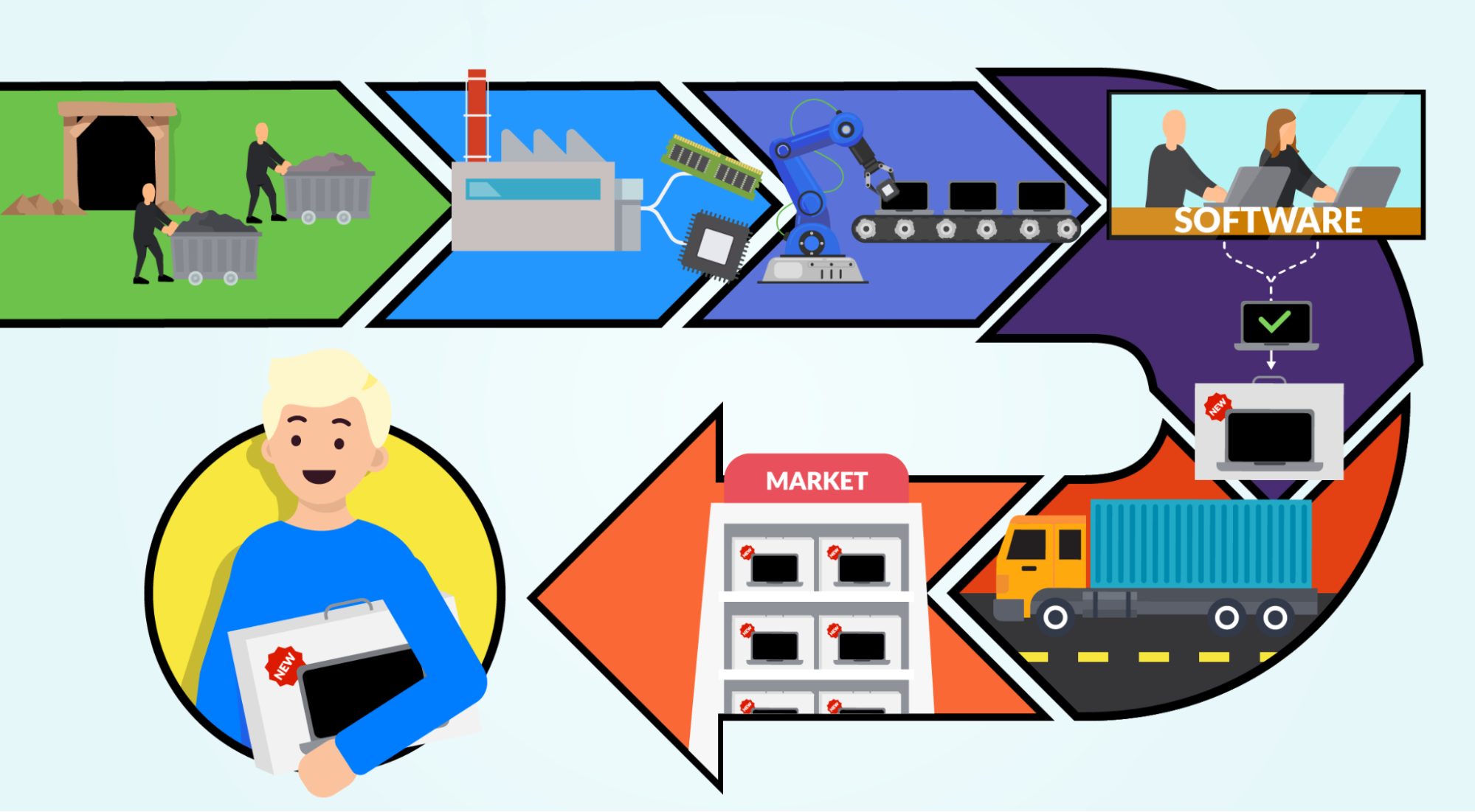
2021 State of the Software Supply Chain: Open Source Security and Dependency Management Take Center Stage
Software Supply Chain Security Ppt Powerpoint Presentation Show Picture Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

OMB memorandum works on enhancing security of software supply chain while complying with NIST guidance - Industrial Cyber

ESF Partners, NSA, and CISA Release Software Supply Chain Guidance for Suppliers > National Security Agency/Central Security Service > Article